
What You Need to Know About Encryption
An infographic that shows just how much people struggle with poverty nowadays. It turns out that those living below the poverty line are three times more likely to develop ment.
There are many methods of encrypting information. And even different methods as to whether you are encrypting information to be stored in a file or being used to encrypt information that is being exchanged between computers or streaming film and video to remote screens. This infographic summarises the commonest encryption algorithms and methods that they are used for. Some of the algorithms are used to exchange secret keys (Elliptic Curve) whilst others (AES) are used to encrypt information in files. The commonest and simplest cipher is the Caesar cipher which works by substituting a different letter for the one being used (A becomes F, B becomes G and so on).al illness than those living above the poverty line.
One of the best and effective solutions is encryption. If you don’t have any understanding about the encryption then you need to know. It is the robust security solution that no organization should forget to integrate it for ensuring data security.
Encryption is the process to use an algorithm for transforming information so that it is unreadable for the users who are unauthorized. It is a cryptographic method which can secure the sensitive data like numbers of a credit card by encoding and altering the data into the unreadable ciphertext.
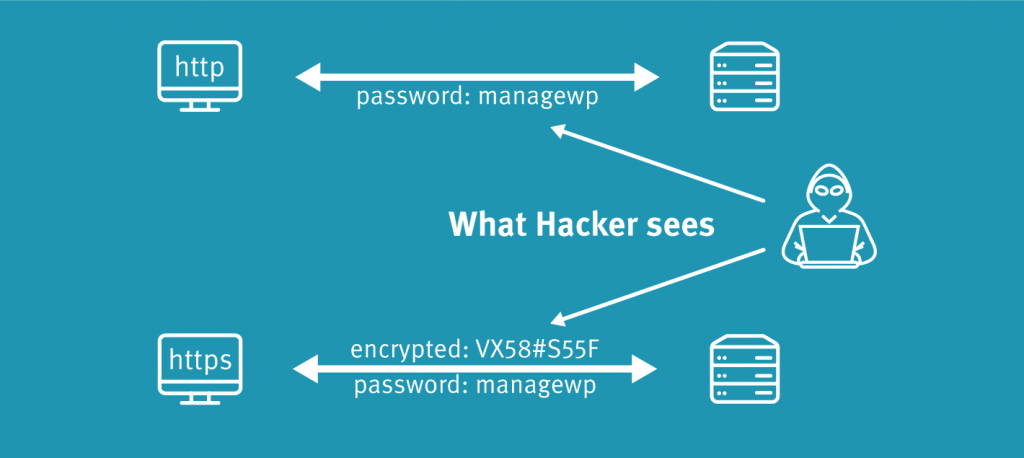
These days the use of encryption security feature is being adopted rapidly for protecting the user information sent between the server and browser. It also integrates the information of payment, passwords, and other private data. Organizations are using this feature for securing their sensitive information stowed in the servers, computers and smart mobile devices.
How does encryption work?
Data that is encrypted is known as plaintext and encryption is ensured with the use of an algorithm and a key. The process includes generating of ciphertext that can be displayed in the original form in case if it is decrypted with the right key. Decryption is the encryption inverse and follows the similar steps but reverses the order of applied keys. There are two algorithms of encryption that are used these days which are symmetric and asymmetric.
Symmetric keys are known as a secret key which includes the use of a single key. It is also known as the shared secret as the system initiating the encryption should share it with any unit it wants to decrypt the data that is encrypted. One of the most used symmetric key ciphers is the AES or Advanced Encryption standard, intended for securing the classified information of government authorities.
Asymmetric key also referred to as public key cryptography. It makes use of the two arithmetic related keys that are public and private. The public key is shareable with anyone whereas this is not the case with the private key. It offers not only aspects like confidentiality but also non-reputability, integrity, and authenticity.
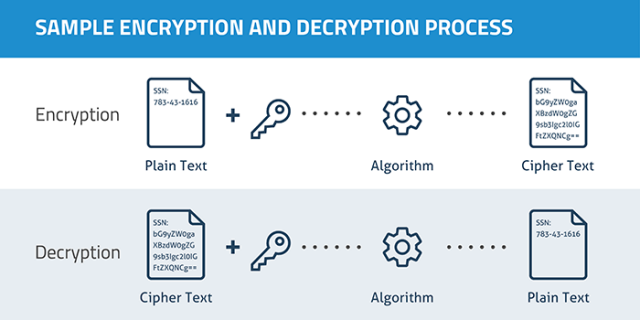
Why should you use encryption?
The primary objective of the encryption is protecting the digital data privacy on the operating systems that are transferring by the internet and other computer networks. Almost every organization recommends the use of encryption security feature for preventing the unauthorized access for the data. Latest encryption algorithm plays a significant role in the IT system security assurance and the communications as they offer not only privacy but also certain vital essentials such as authentication, integrity, and non-repudiation.




